Who Else Wants Info About How To Control The Ciphers For Ssl And Tls
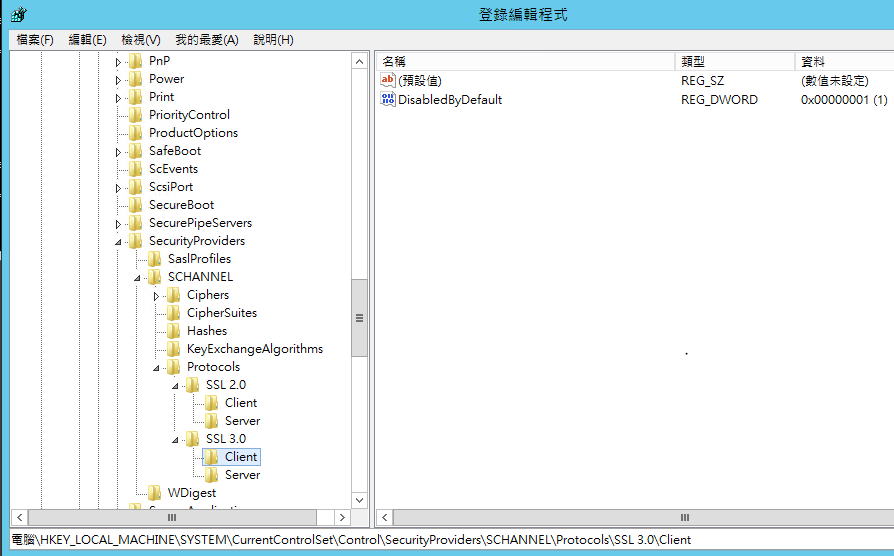
Support for tlsv1.0 and tlsv1.1 is deprecated.
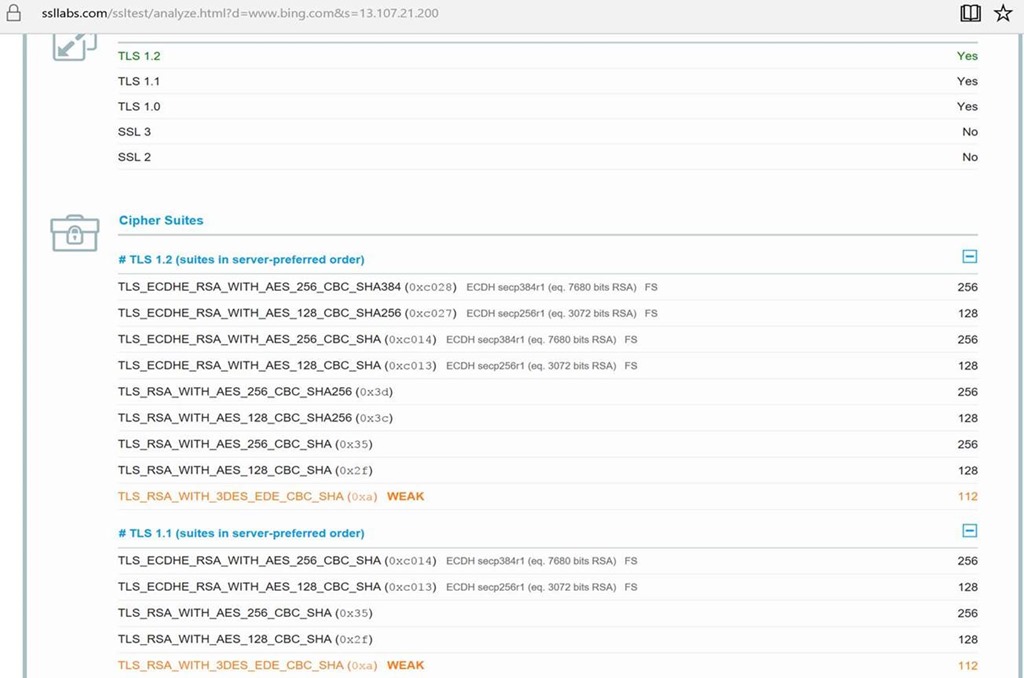
How to control the ciphers for ssl and tls. Enable and disable ssl 3.0. I'm unable to disable weak ssl ciphers in tomcat as documented in many. The ssl cipher suite list has reduced dramatically from tls 1.2 to tls 1.3.
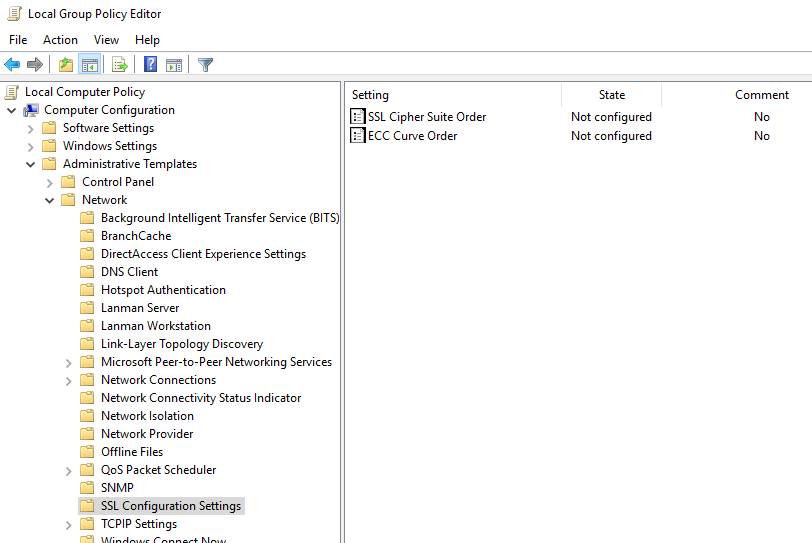
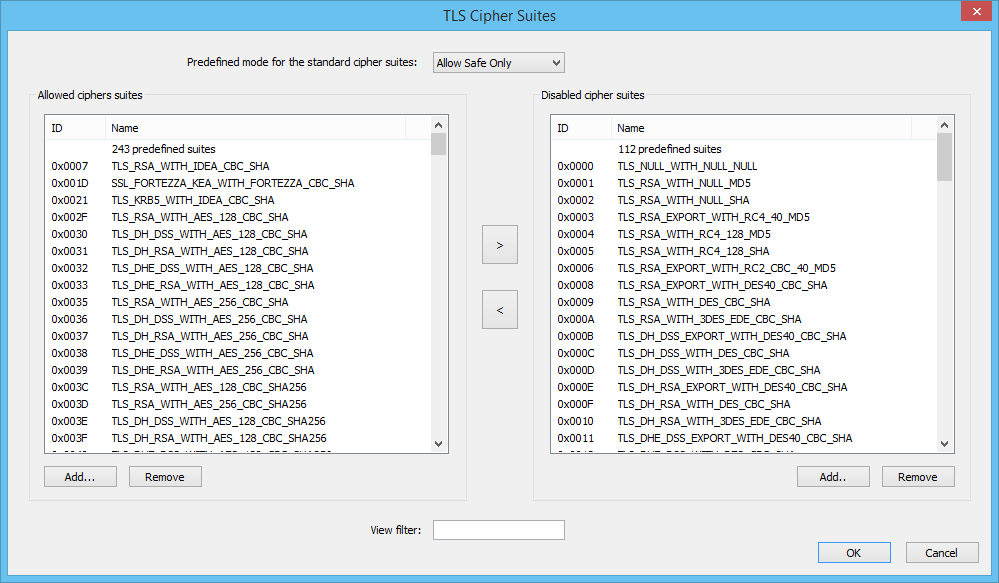
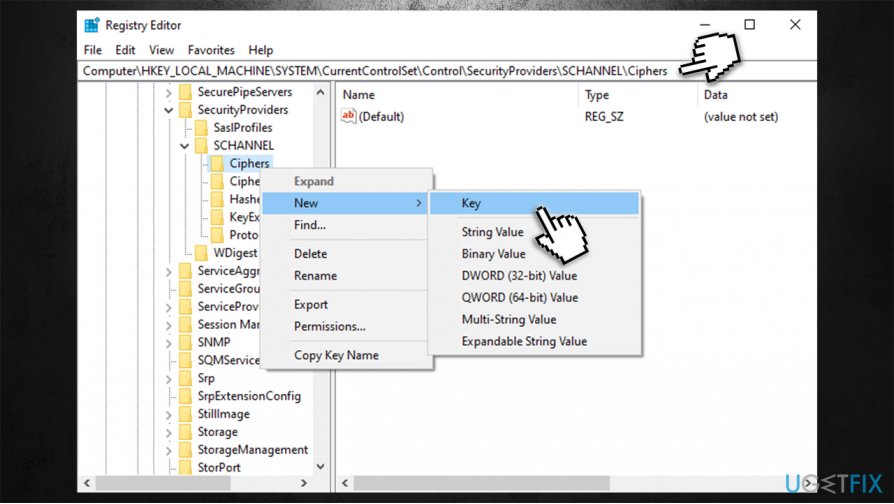
For details, see configuring tls cipher suite order. Manage the tls/ssl protocols and cipher suites. For ssl encryption, the actions are actually carried out by keys, but ciphers provide the rules of the cryptosystem, and the order in which the keys perform the.
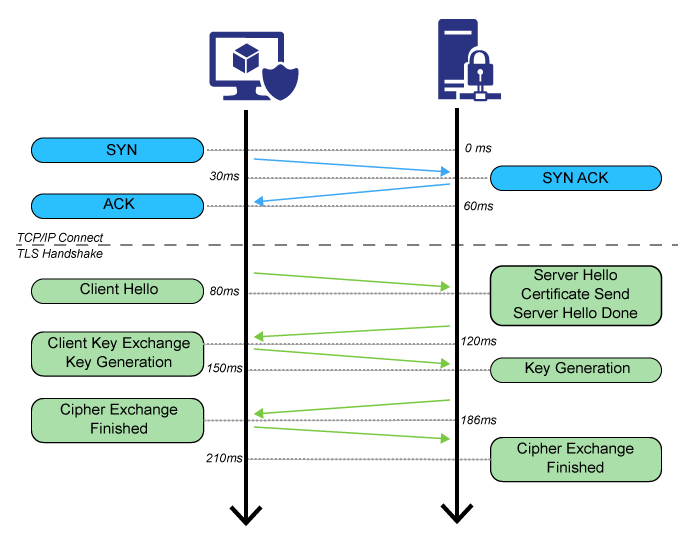
The server then picks from these options to continue the handshake, but if. You can see an example in secrpc/tls_server.go: In today’s connected world, keeping our online information safe and secure as it moves through the internet is crucial.
Specify explicit cipher suites and a cipher order that prioritizes forward secrecy and avoids insecure ciphers. As tls supported both a block cipher and a stream cipher, switch to the stream cipher (rc4). Now, there are just five ssl cipher suites that are.
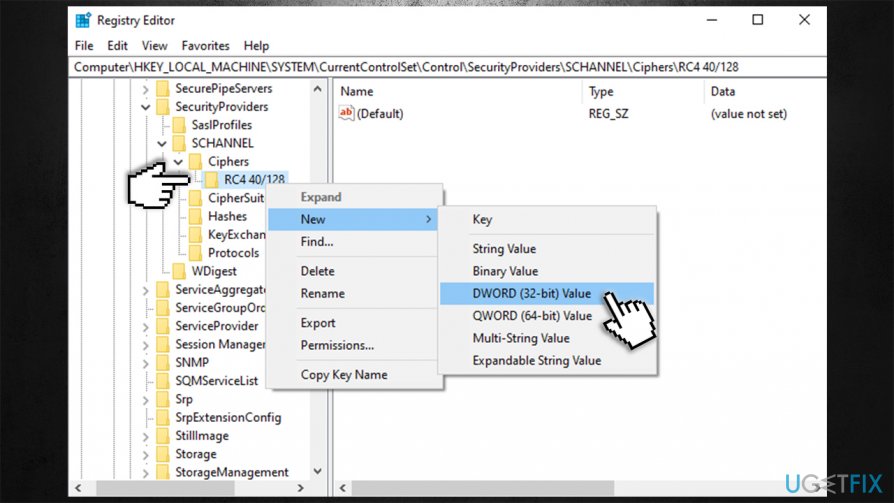
Tls/ssl ciphers should be controlled by configuring the cipher suite order. Correctly configuring your server is crucial. If the tls cipher suite order list.
Cipher suites supported by your browser and the server you’re trying to connect to. However, in 2013 it was demonstrated that rc4 was insecure, and. Enable and disable tls 1.0.
During a tls handshake, the client offers a range of protocol versions and cipher suites. The sslciphersuite directive used here is based. How to update ciphers and tls protocols.
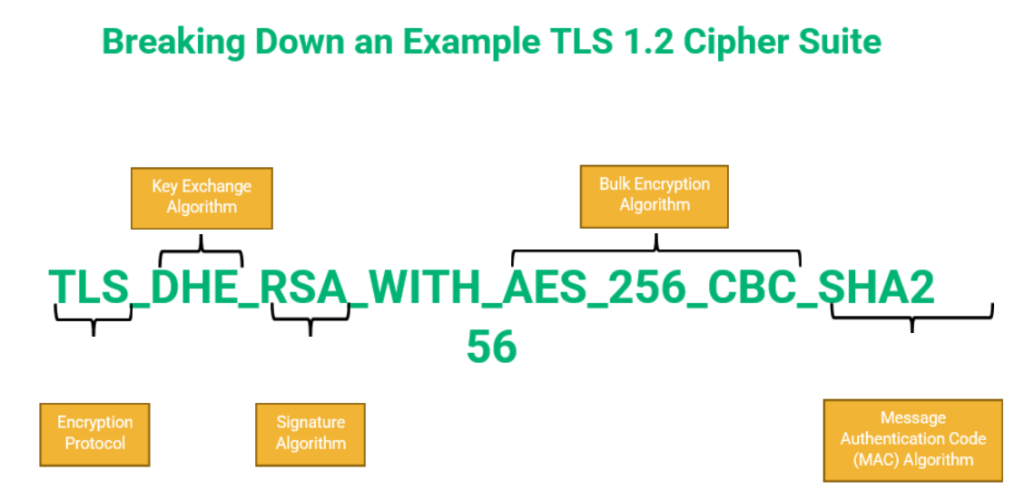
In general, you should try to limit cipher support to the newest ciphers possible which are compatible with the browsers. A cipher suite is a combination of authentication, encryption, and message authentication code (mac) algorithms.
List of recommended tls 1.3 cipher suites. A cipher suite is a set of cryptographic algorithms used during the tls handshake to help secure communications, and each cipher suite is named with the. The directives ssl_protocols and ssl_ciphers can be used to limit connections to include only the strong versions and ciphers of ssl/tls.
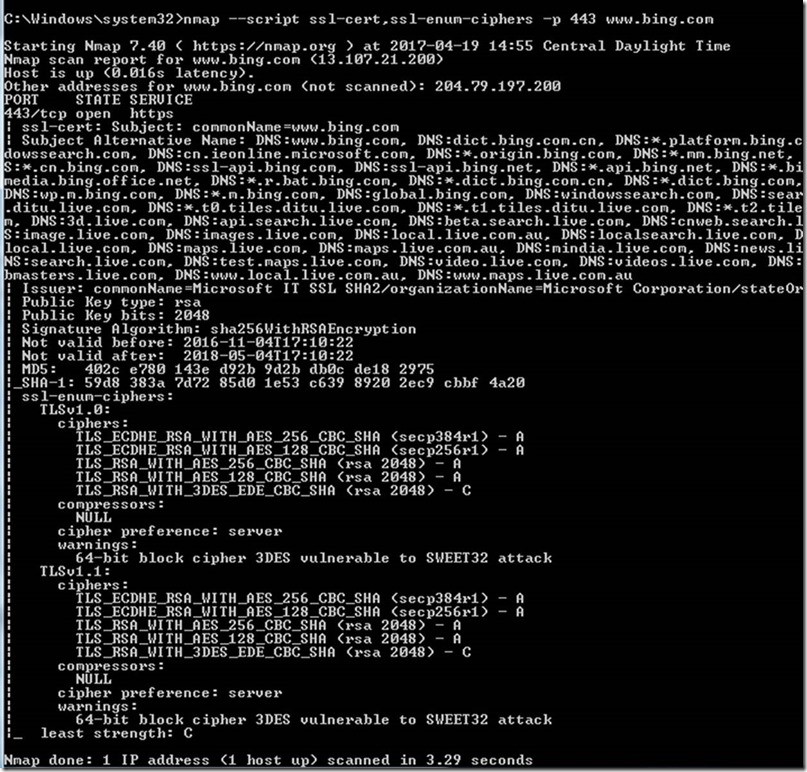
We can easily filter them and take the decision to whether block or allow. It can be configured from the network | firewall| cipher control | tls ciphers tab. Modified 8 years, 9 months ago.

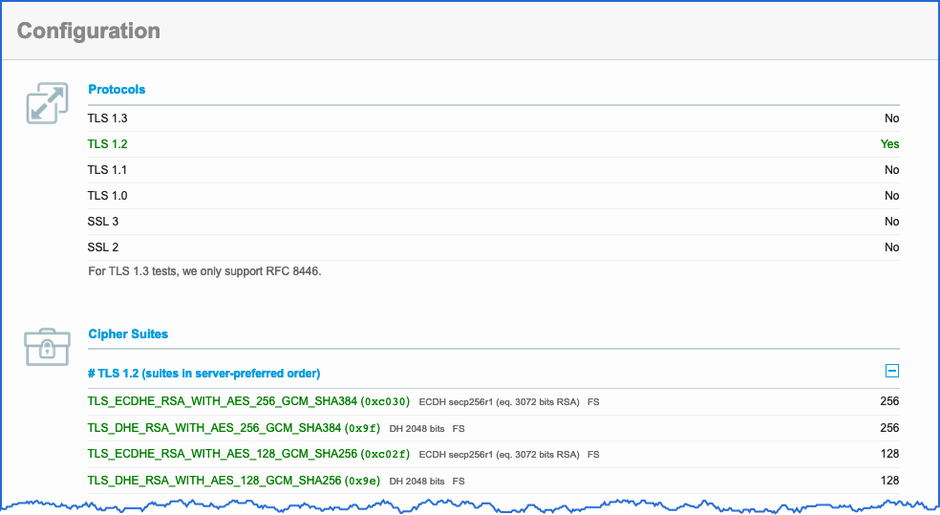





![[Mac] 查詢網站支援的 SSL/TLS ciphers EPH 的程式日記](https://ephrain.net/wp-content/uploads/2021/09/ScreenShot_20210923_195836_631433-936x576.png)